Symmetry | Free Full-Text | Comprehensive Survey of Multimedia Steganalysis: Techniques, Evaluations, and Trends in Future Research

A comparative analysis of image steganography based on DCT algorithm and steganography tool to hide nuclear reactors confidential information - ScienceDirect
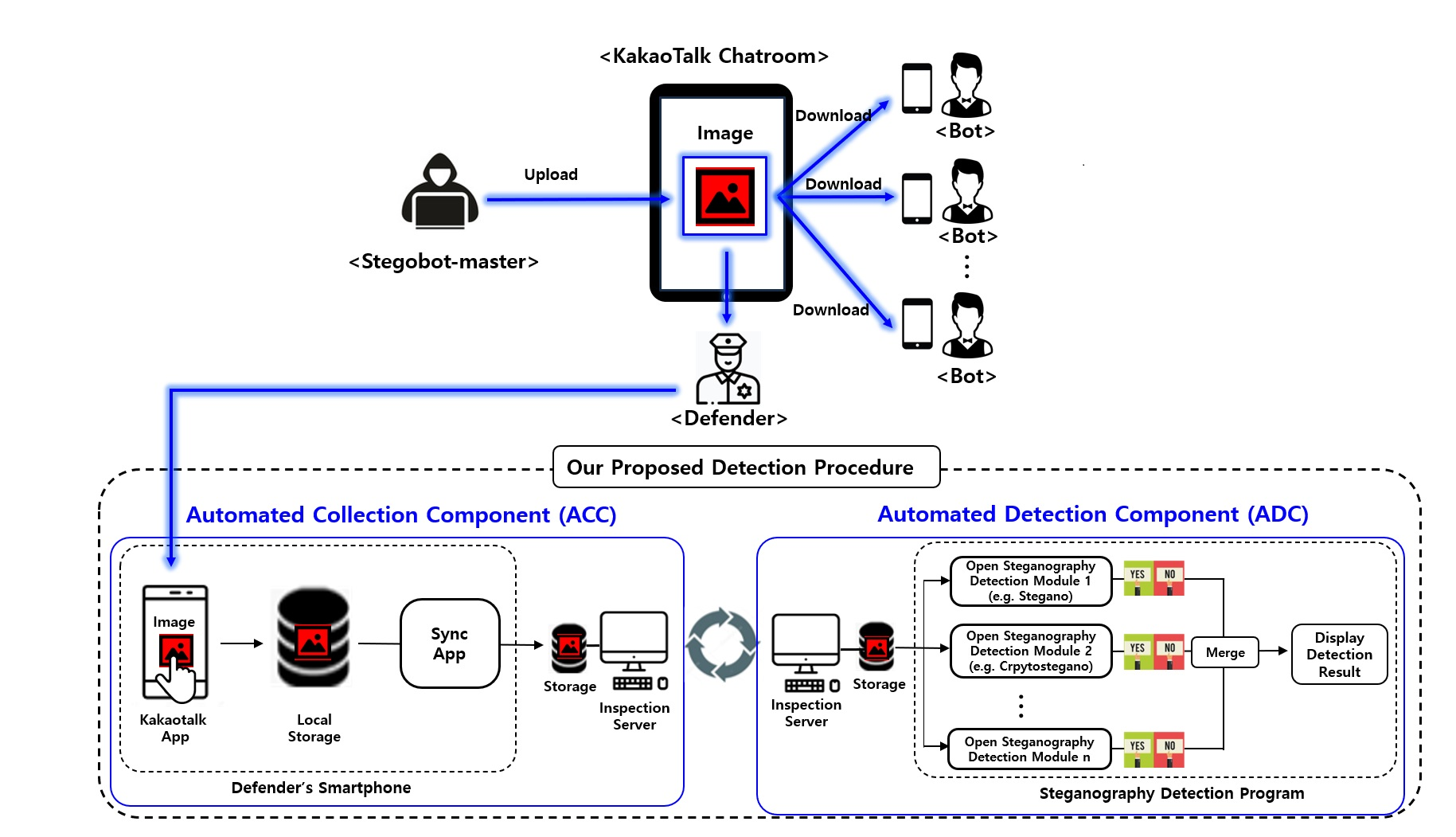
Computers | Free Full-Text | Design and Implementation of Automated Steganography Image-Detection System for the KakaoTalk Instant Messenger

A review on image steganographic techniques based on optimization algorithms for secret communication | Multimedia Tools and Applications
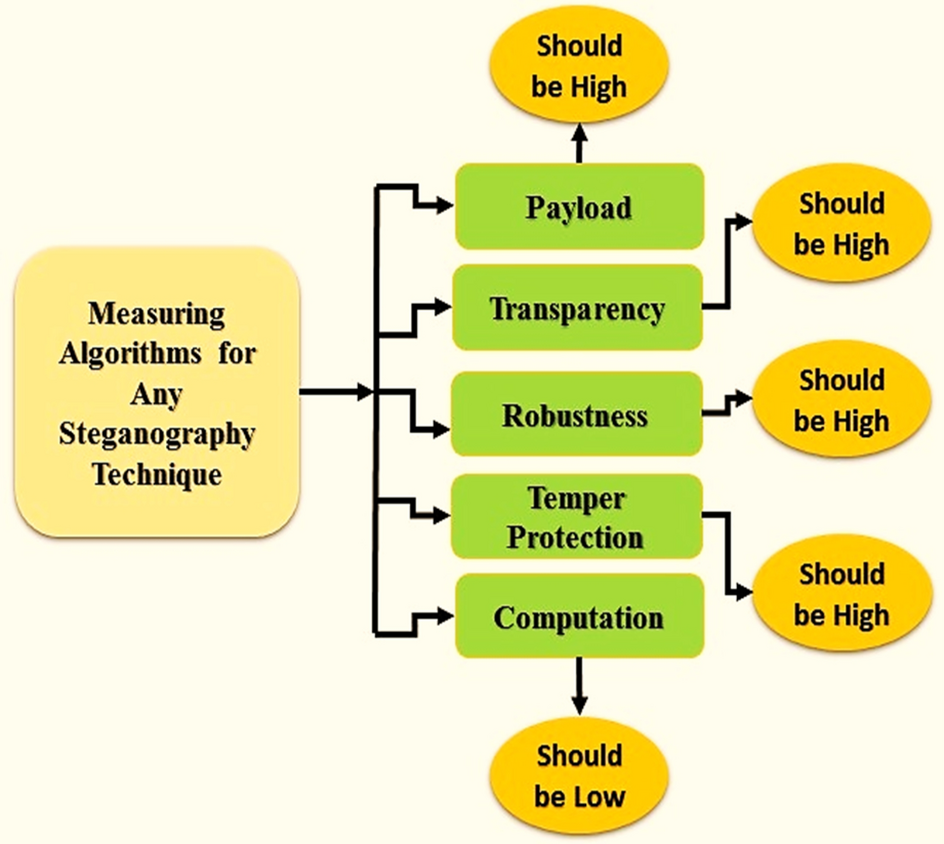
A Huffman code LSB based image steganography technique using multi-level encryption and achromatic component of an image | Scientific Reports
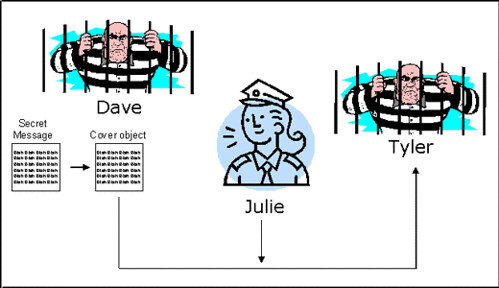

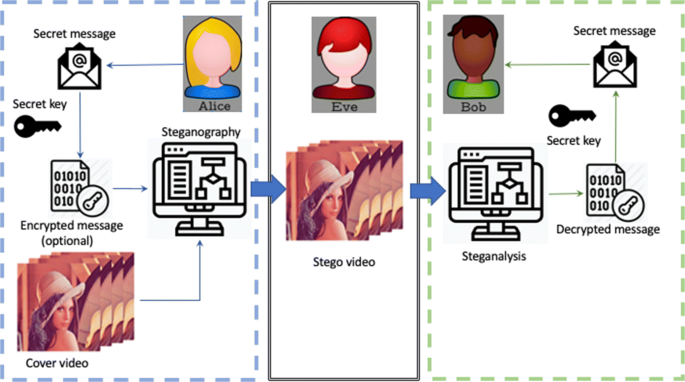
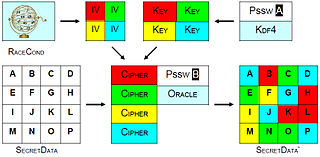



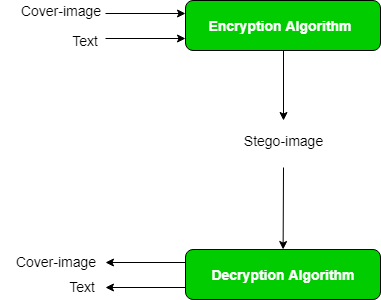
.png)