Cloud Computing Authentication Methods Ppt Powerpoint Presentation Ideas Deck Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
![Managing identification, authentication, and authorization in the cloud computing environment - Information Security Handbook [Book] Managing identification, authentication, and authorization in the cloud computing environment - Information Security Handbook [Book]](https://www.oreilly.com/api/v2/epubs/9781788478830/files/assets/8ea6aea9-f5a9-423b-a968-dc8aec69e0ca.png)
Managing identification, authentication, and authorization in the cloud computing environment - Information Security Handbook [Book]

Cloud Authentication Gateway Cloud Computing Standard Architecture Patterns Ppt Slide | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

Sensors | Free Full-Text | A Blockchain-Based Authentication and Authorization Scheme for Distributed Mobile Cloud Computing Services
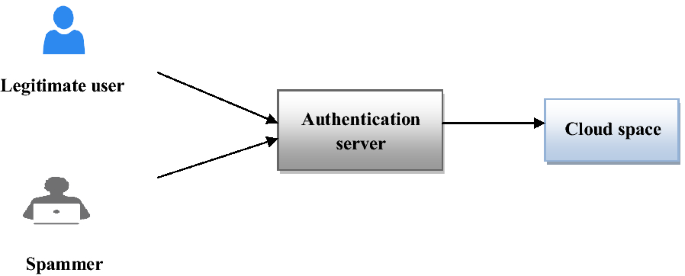
Ensuring user authentication and data integrity in multi-cloud environment | Human-centric Computing and Information Sciences | Full Text

Identity management Cloud computing security Authentication Software as a service Access control, cloud computing, text, public Relations, logo png | PNGWing

AUTHENTICATION OF USER IN CLOUD COMPUTING Dr. Nilesh Mahajan1, Mrs. Devyani Patil2 by bvimed.publications - Issuu